John Ralls is our webmaster and chair of the Technology and Website Committee
There’s a particularly bad form of email fraud going around this fall that poses two serious risks: More widely, that you might be tricked by a gift-card scam because it appears to come from someone you know and trust. For a very unfortunate few, that you might lose control of your primary email account to have it used to perpetrate the scam. I know of four such attacks in the last month, two of which involved CGS members having their email accounts taken over. The other two were volunteers at other non-profits that I volunteer for.
The Gift Card Scam
This is a variant of the family emergency scam, one of many that Amazon.com warns about on this comprehensive page. The first email typically asks something like “do you shop at Amazon.com?” or “are you an Amazon prime member?”. If you reply a followup will ask you as a favor to buy the supposed sender a gift card for which they’ll reimburse you.
For most of us the first line of defense when we get a suspicious email like that is to check the From: address to see if it’s really our friend’s address. Most of the time it’s not and we delete it and move on. In this scam campaign it really will be the right address because the criminals have taken over the account.
On the emails I’ve seen there is a sign that it’s not legitimate: They have a “Reply-To:” address set, usually to the same user as the “From:” address but on a different service. For example, the From: address might be [email protected] and the Reply-To: address [email protected]. My usual email client (Apple Mail) automatically displays the extra address if it’s present. The GMail web interface will display it if you click the little reveal arrow next to the sender. Below is an illustration:
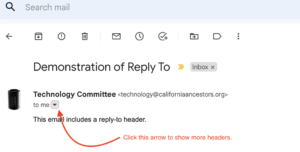
It will show you more information about the email:
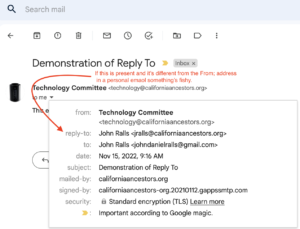
If you see a “reply-to” entry that means that if you just click “reply” the email will go to that address instead of the From address. For a personal email from an individual, that’s suspicious. The scammers use that to try to keep replies from alerting the original owner to the scam.
If you get one of these emails don’t reply to it and don’t try to use the “From:” address either. In three of the four cases I saw recently, the email account had been taken over by the criminal. In at least one case the criminal had taken over the user’s cell phone and used it to take over all of the user’s email accounts. The safest way to tell someone their email has been hacked is to visit them in person or telephone them on their land-line phone. I don’t recommend trying to use the victim’s cell phone number because if it has been compromised that will reveal your phone number to the criminal.
Secure your own email account
The other important thing is to protect your email address against being taken over. The best protection is the standard security advice: Use a strong password generated by a password manager. If your computers (that phone in your pocket is really a computer that happens to be able to do cellular voice communication) have fingerprint or face recognition, use it. If your email provider supports two-factor authentication, turn it on. Prefer using an authenticator app over text messages: It’s possible for a criminal to take over your phone number and get your text messages, but using an authenticator app requires physical posession of the computer it’s installed on.
Always practice good security hygiene. Never click on a link you receive in email unless you’re absolutely sure that you know and trust the sender. Keep your software up to date, especially the operating system and web browser. If your computer, including the one you call a phone, is so old that it’s not getting updates any more then it needs to be replaced. Note that users of Microsoft Windows computers that can’t run Windows 10 or Windows 11 can install ChromeOS or Linux instead and resume getting security updates. Use a password manager and let it generate passwords for you. All of the current web browsers have one built in. Don’t reuse passwords between websites, to limit the damage if one gets compromised, and change the important ones periodically, where important means that there’s money or important personal information attached.
NOV
2022
